Web3: Easily Adding the Concept of Wallet to a Web2 Authentication
Alexandre Petit9 min read

The adoption of blockchain technology and web3 is rapidly growing but still remains an obscure field for developers. It is quite possible that as a developer on your next project, you may be asked to have your users interact with a blockchain, for example, to store NFTs or to simply communicate with a smart contract. If you need to add this concept of a wallet to your web application, you have understood the previous jargon but do not quite know how to go about it, then this article is for you 😎
Before we start, it seems essential to give a little reminder about what a custodial wallet and a non-custodial wallet are:
Custodial: Private key stored on a remote server
Non-custodial: Private key stored by the user
To learn more 👉 Custodial vs. Non-Custodial Wallets: What is the Difference? | Binance Academy
It is important to know that cryptocurrency wallets are often seen as a major obstacle to blockchain adoption by the general public. For an average user, creating and managing a wallet can be complex and intimidating tasks. As a developer, it is therefore important to find ways to make this ownership and usage completely transparent.
In this article, first we will explore the different ways to integrate the concept of a wallet into a web2 authentication, comparing custodial and non-custodial solutions before focusing on key management solutions. Then, we will specifically look at how key management solutions can address transparency issues for users and decentralization of public and private keys. And finally, we will conclude with a comparison of the two most commonly used key management solutions, namely Web3Auth and Magic.
Custodial or non-custodial ?

Custodial
Custodial wallets, such as Coinbase Wallet, or wallets offered by your favorite exchanges, offer a simple user experience because the user does not need to install an extension or application such as Metamask or TrustWallet, or even use a third-party service, the management and use of your private keys associated with your wallet is entirely managed by the platform. However, this means that the private keys are stored on centralized servers, which presents a potential security risk. As a developer, setting up a secure and reliable infrastructure for managing and/or storing users’ public and private keys is an extremely complex task that requires significant initial and ongoing maintenance costs.
Non-custodial
Non-custodial wallets, such as Metamask, offer a more complex user experience because the user must store their private keys locally and manage all their transactions themselves. However, as a developer, this means that the private keys are entirely under the control of the user, allowing you to absolve yourself of any responsibility in case of a potential hack. It is also important to note that there are many wallet providers, and each one may require individual adaptation. Since there is no need for a dedicated key storage infrastructure, the cost of implementation is almost zero.
Comparison
| Wallet solution | Custodial | Non-custodial |
|---|---|---|
| User experience | ⭐️⭐️⭐️ __ The user does not have to install any extension or manage their keys himself | ⭐️ __ - Complex wallet creation - The user must install an extension or manage their private keys themselves |
| Authentication integration | ⭐️⭐️⭐️ __ Classic web2 authentication | ⭐️⭐️ __ - New authentication flow - Management of user cases with / without wallet - Each wallet provider has a different implementation |
| Responsibility | ⭐️ __ Application responsible for private keys | ⭐️⭐️⭐️ __ The user is responsible for storing their private keys |
| Infrastructure costs | ⭐️ __ Setting up an infrastructure to secure and store private keys is a very complex task | ⭐️⭐️⭐️ __ Apart from the development, there is no additional cost |
| Decentralization | - __ Fully centralized | ⭐️⭐️⭐️ __ Fully decentralized |
Summary of the comparison
To summarize, integrating a custodial wallet solution will be pleasant for the user as the wallet concept is almost transparent, but it remains centralized and entails significant costs and responsibilities related to your users’ keys. On the other hand, a non-custodial wallet solution will be more difficult for the user to access (installation of an extension, application, seed phrases, additional password…) but remains decentralized and frees you from any responsibility in case of hacking.
Presentation of key management solutions

Fortunately, key management solutions exist and provide non-custodial wallets without requiring users to create a wallet or install an application. To do so, they offer developers a Software-as-a-Service (SaaS) solution, which, coupled with an existing authentication (Social logins, OAuth 2, Passwordless authentication, etc.), provides a wallet. These solutions perfectly address user experience, security, and decentralization issues.
To date, the two market leaders are Magic and Web3Auth, both of which adopt a different approach in managing users’ private keys.
How does Web3Auth work?
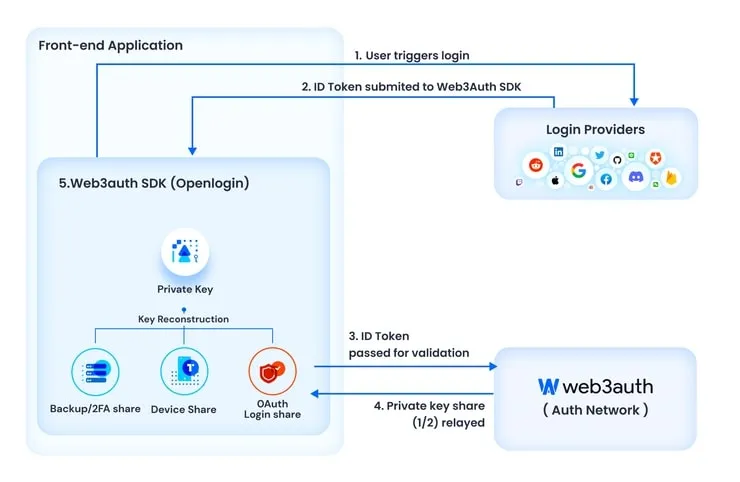
I invite you to watch this 2-min video that explains how Web3Auth manages keys in a decentralized way. To put it simply, Web3Auth uses a cryptographic algorithm called Shamir Secret Sharing (SSS) to split the private key into several MPC (Multi-Party Computation) parts, and it is possible to reconstruct it with only 2 of these parts. The private key is not stored on a server but is directly reconstructed by the front-end, making it a non-custodial wallet solution.
These 2 key parts can be:
- 1 connection provider
- 1 backup on a device
- 1 backup: to download, backup email, or a security question
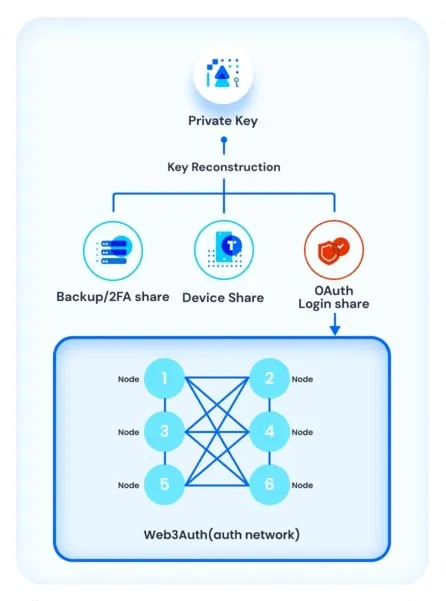
Key generation is done through a consensus system that has 9 nodes. If the token passed for validation is verified on at least 5 nodes, then the private key can be reconstructed.
Note that it is possible to add as many devices as desired and each device is considered as a part of the private key. Therefore, only 2 devices are needed to rebuild the key in case of loss.
📖 Documentation for Web3Auth 👉 https://docs.web3auth.com/
How does Magic work?
Some vocabulary before reading further:
AWS KMS: Key Management Service: Encryption and cryptographic key management service
AWS HSM: Hardware Security Module: Secure storage of cryptographic keys
AWS Cognito: Service providing authentication, authorization, and user management
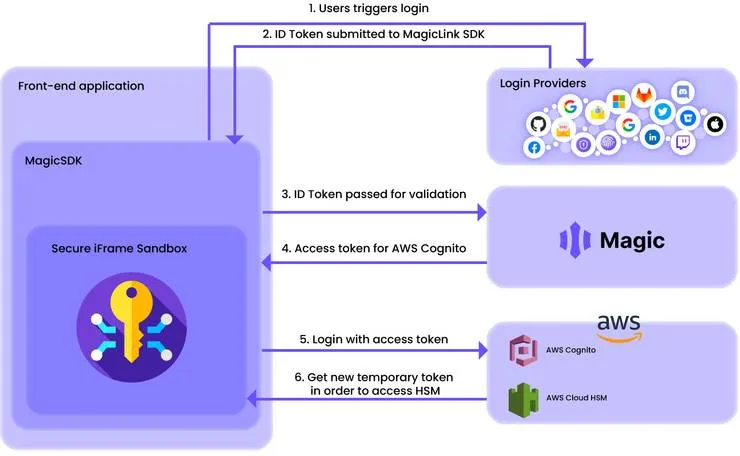
To preserve the security of user keys, Magic uses a technique that combines a delegated key management system (currently being patented) and hardware security modules provided by Amazon Web Services (AWS HSM).
The delegated key management system is a method that allows, as its name suggests, delegating encryption and decryption tasks to AWS KMS and AWS Cognito. Users’ private keys are stored in hardware security modules (HSMs) provided by AWS KMS. The HSMs store the hardware master keys that allow generating the private keys transmitted to users. These hardware master keys cannot be exported and remain within the hardware, so all encryption and decryption operations take place within the hardware.
When a user authenticates with the Magic authentication relay, they receive a temporary access token allowing them to connect to AWS Cognito, which, once connected, returns time-limited credentials to perform operations in the HSM. This allows the client to interact directly with AWS to access their private keys stored on the HSM, completely bypassing Magic’s backend. This mechanism prevents interception or falsification of limited credentials.
Comparison
| Aspect | Web3Auth | Magic |
|---|---|---|
| Wallet management | ⭐️⭐️⭐️ __ Non-custodial Multi-Party Calculation (MPC) Solution | ⭐️⭐️ __ Semi-custodial solution based on Amazon Web Service (AWS) hardware security modules (HSM) |
| Authentication features | ⭐️⭐️⭐️ __ - Social login (10+) - Coinbase Wallet - Metamask - WalletConnect - Torus Wallet - Identity providers (Auth0, AWS Cognito, Firebase, Okta) - Email Magic Link - SMS Login - WebAuthn - 2FA - Custom implementation | ⭐️⭐️ __ - Social login (10+) - Coinbase Wallet - Metamask - Email Magic Link - SMS Login - WebAuthn - 2FA |
| Blockchain supported | ⭐️⭐️⭐️ __ SDKs are blockchain agnostic, meaning they can be used on any blockchain. | ⭐️⭐️ __ Supports over 20 popular blockchains. |
| Personalization and branding | ⭐️⭐️⭐️ __ Allows applications and wallets to customize and whitelabel the solution. | ⭐️⭐️ __ Provides a range of customization options, but is limited compared to Web3Auth. |
| Ease of integration | ⭐️⭐️ __ Easy to set up connection modal. Has an integration builder | ⭐️⭐️⭐️ __ Easy to set up connection modal + very good documentation. |
| Interoperability | ⭐️⭐️ __ With Tor.us, your users have the ability to use their wallets on other decentralized applications via WalletConnect | ⭐️⭐️⭐️ __ Possibility to export the private key with the Magic Auth solution. |
| Cost | ⭐️⭐️⭐️ __ In the form of packages with a quota of MAW* included + a variable rate for additional MAW. Free subscription includes 1000 MAW + $0.04 per additional MAW. Comes to an average of $0.04 MAW | ⭐️⭐️ __ 0.05 per MAU** up to 5000 MAUs then 0.10 Magic Auth Plus subscription at 199$/month to unlock some features like 2FA |
* 1 Monthly Active Wallet (MAW)= 5 logins/transactions per unique wallet per month
Formula: Total logins/transactions divided by 5 = Total MAWs
** 1 Monthly Active User (MAU)= Any user who signs up or logs in to any of your apps via email, SMS, or social login during a given calendar month.
Note: Users who connect via MetaMask, WalletConnect, or other third-party wallets are not counted as monthly active users.
For more information, I invite you to read this article written by Web3Auth 👉 Web3Auth vs Magic — How to choose your Key Management Solution
In summary, both solutions provide comparable authentication methods, but primarily differ in their key management and blockchain support. The most suitable option depends on your specific requirements. If your project prioritizes interoperability and the ability for users to export their private keys, Magic might be the better choice. On the other hand, if cost, compatibility with a blockchain not supported by Magic, or the necessity for fully decentralized authentication are crucial factors, Web3Auth would be a more fitting solution.
📖 Documentation for Magic 👉 https://docs.magic.link/
Conclusion
The choice of solution depends on your specific needs and those of your users. Take the time to evaluate the different options and choose the one that best suits your project and objectives.
Generally, if you have the resources, time, and/or specific requirements regarding your users’ wallets, then custodial wallets might be more appropriate.
If your users already have their own wallets and are familiar with them, then a non-custodial solution will be more suitable.
However, if your users do not have a wallet and you want to provide them with one when they connect to your application, then a key management solution will be more suitable.
Note that key management solutions, such as Magic and Web3Auth, represent a major evolution in the blockchain ecosystem, as they combine the advantages of custodial and non-custodial wallets. By offering a simplified user experience, while maintaining a high level of security and decentralization, these solutions facilitate the adoption of blockchain technology by the general public and allow developers to easily integrate blockchain features into their existing Web2 applications.
If you are curious about how to integrate Magic or Web3Auth with Web2 authentication, feel free to let me know in the comments!
Looking forward to reading your comments and happy coding!